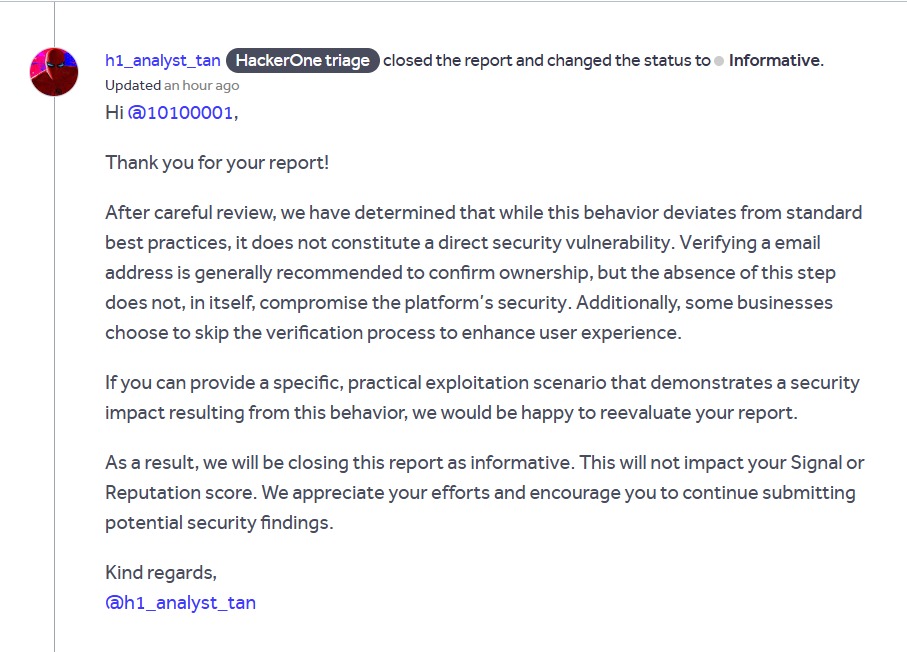
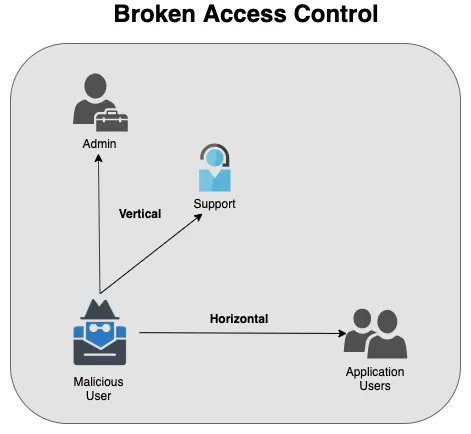
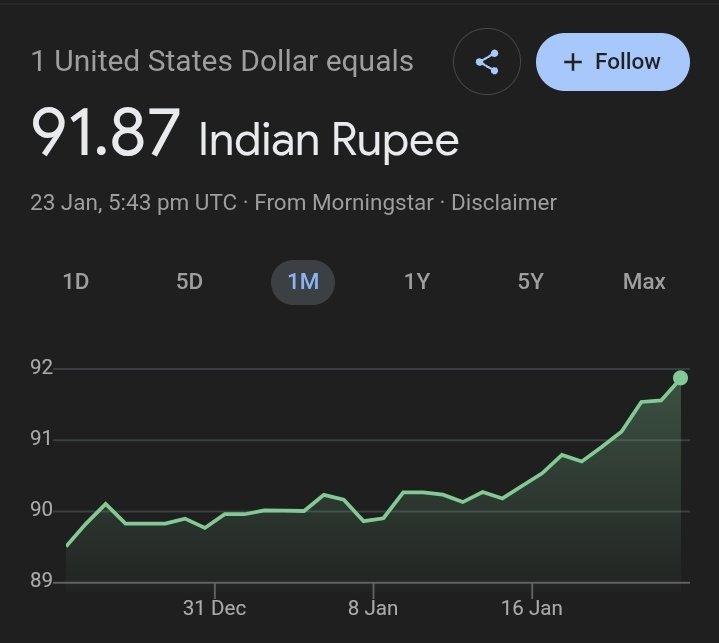
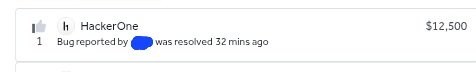
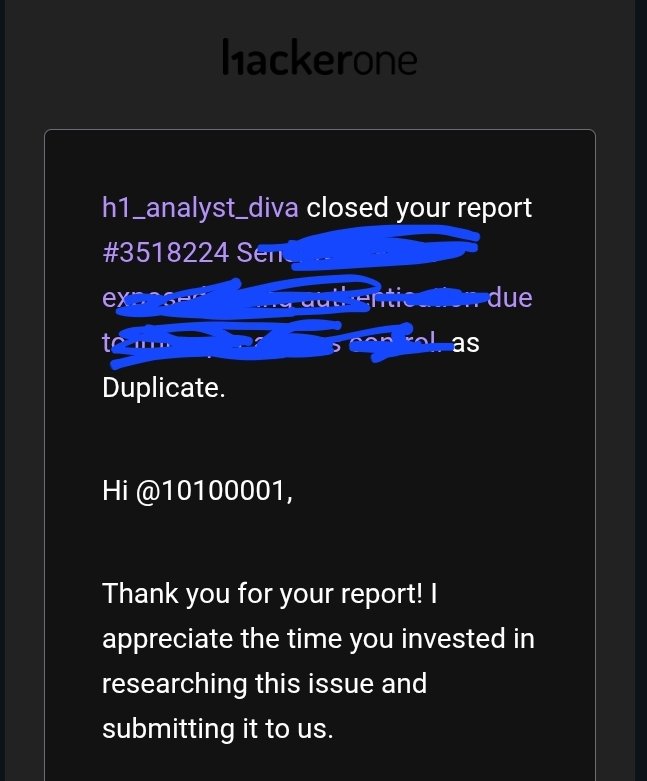
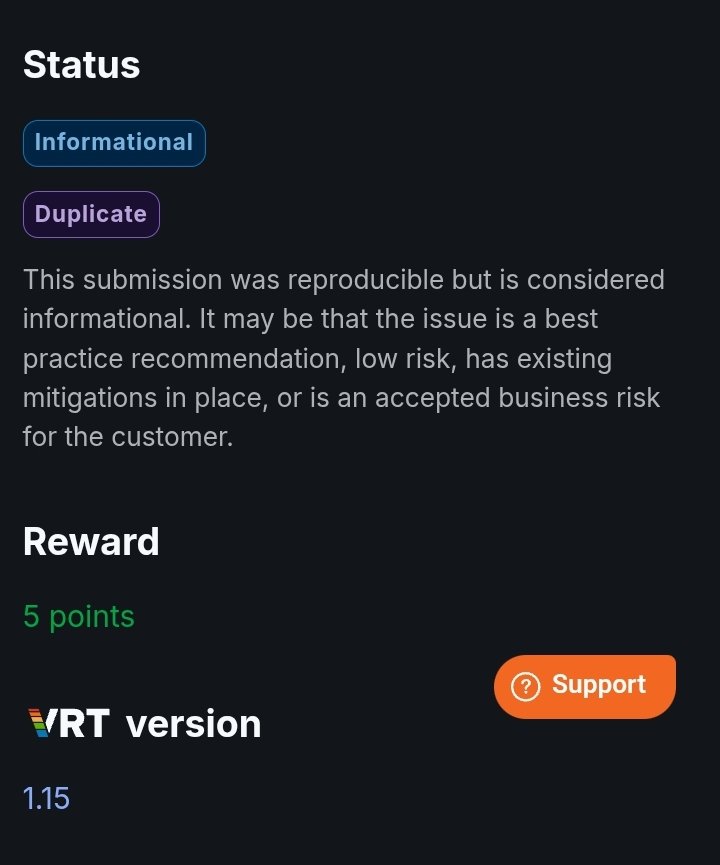
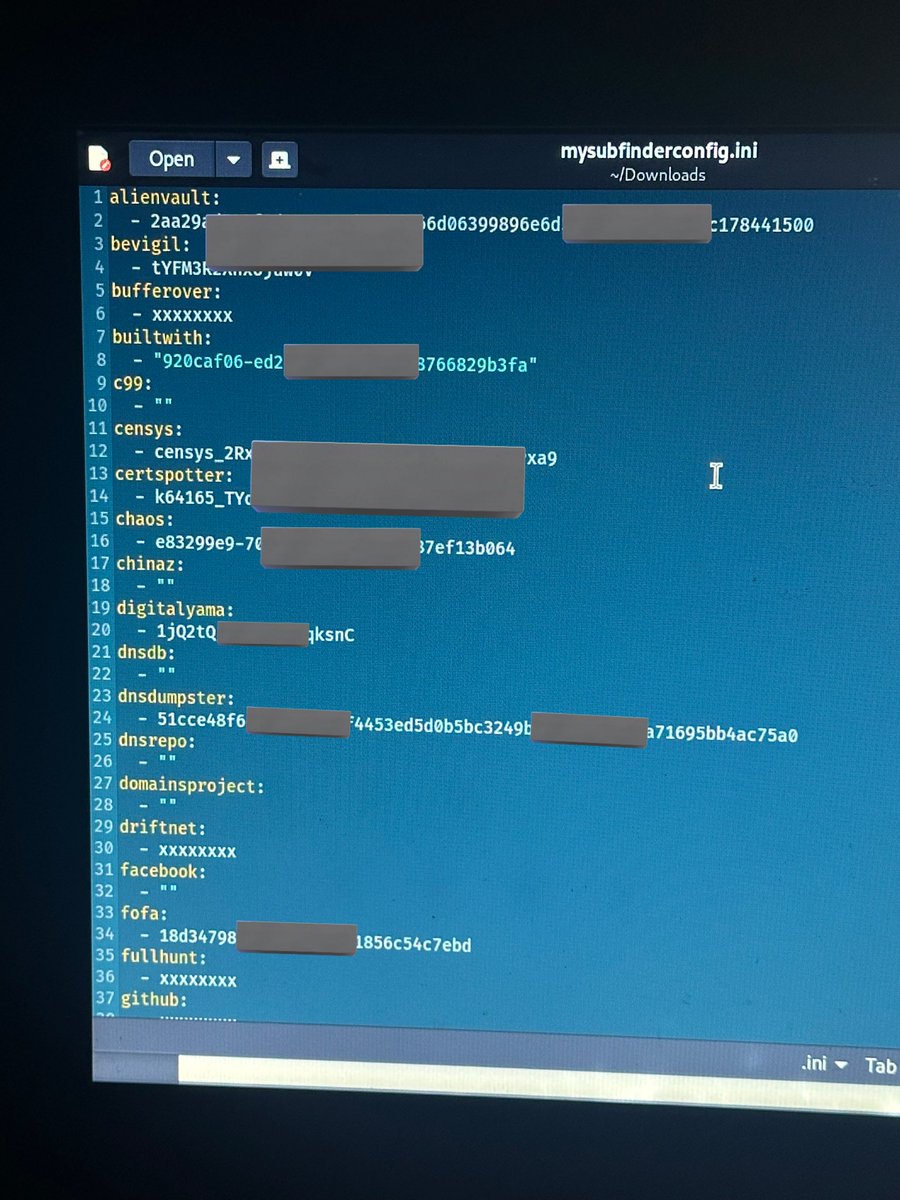
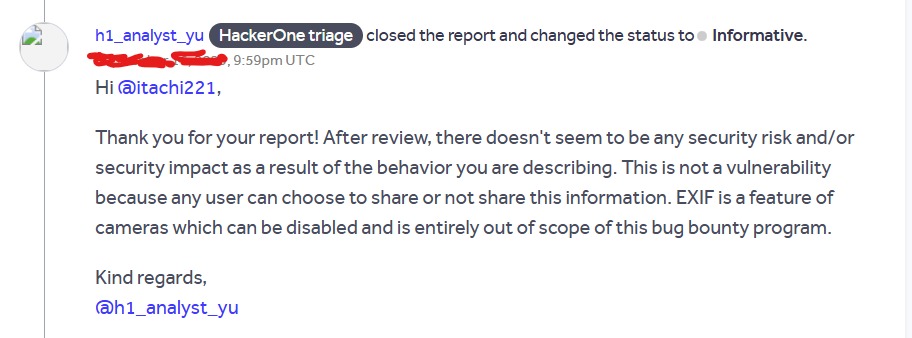
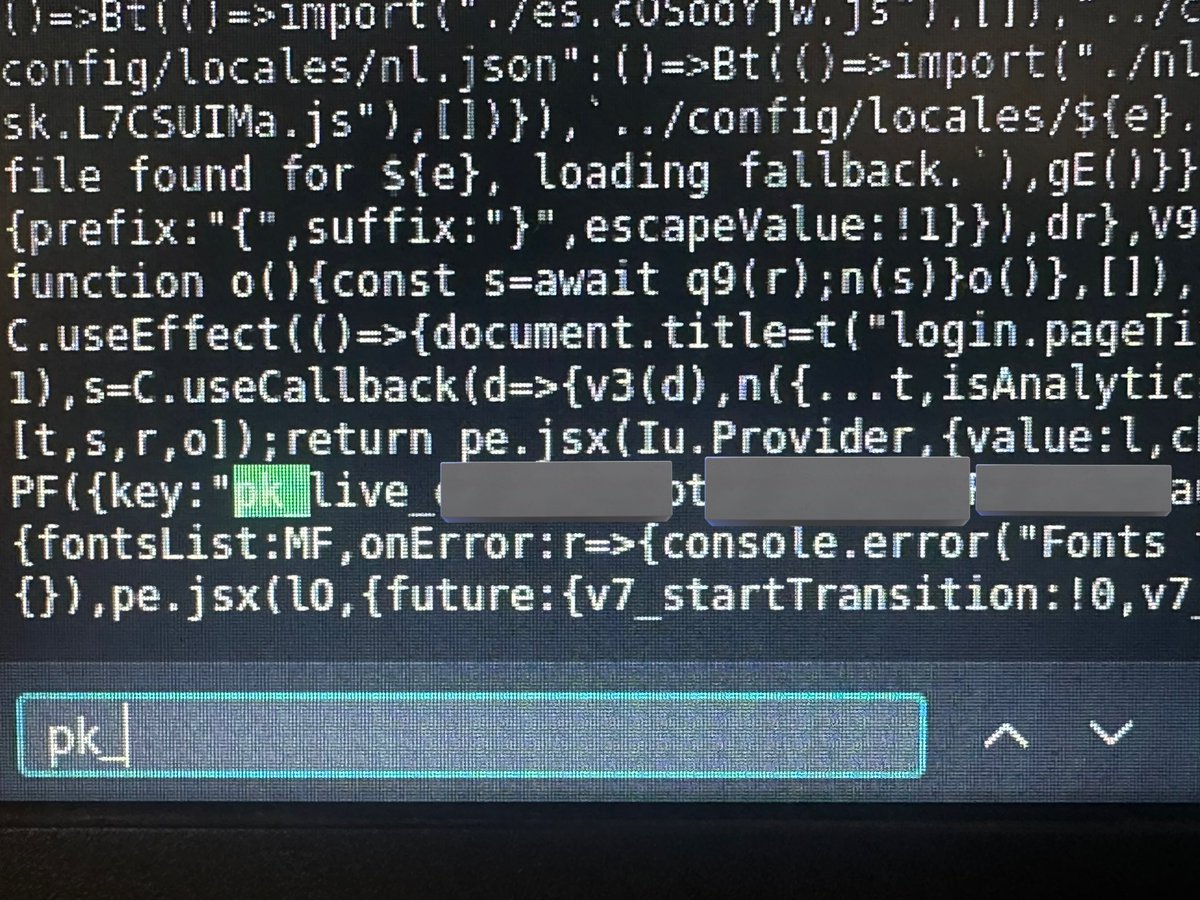
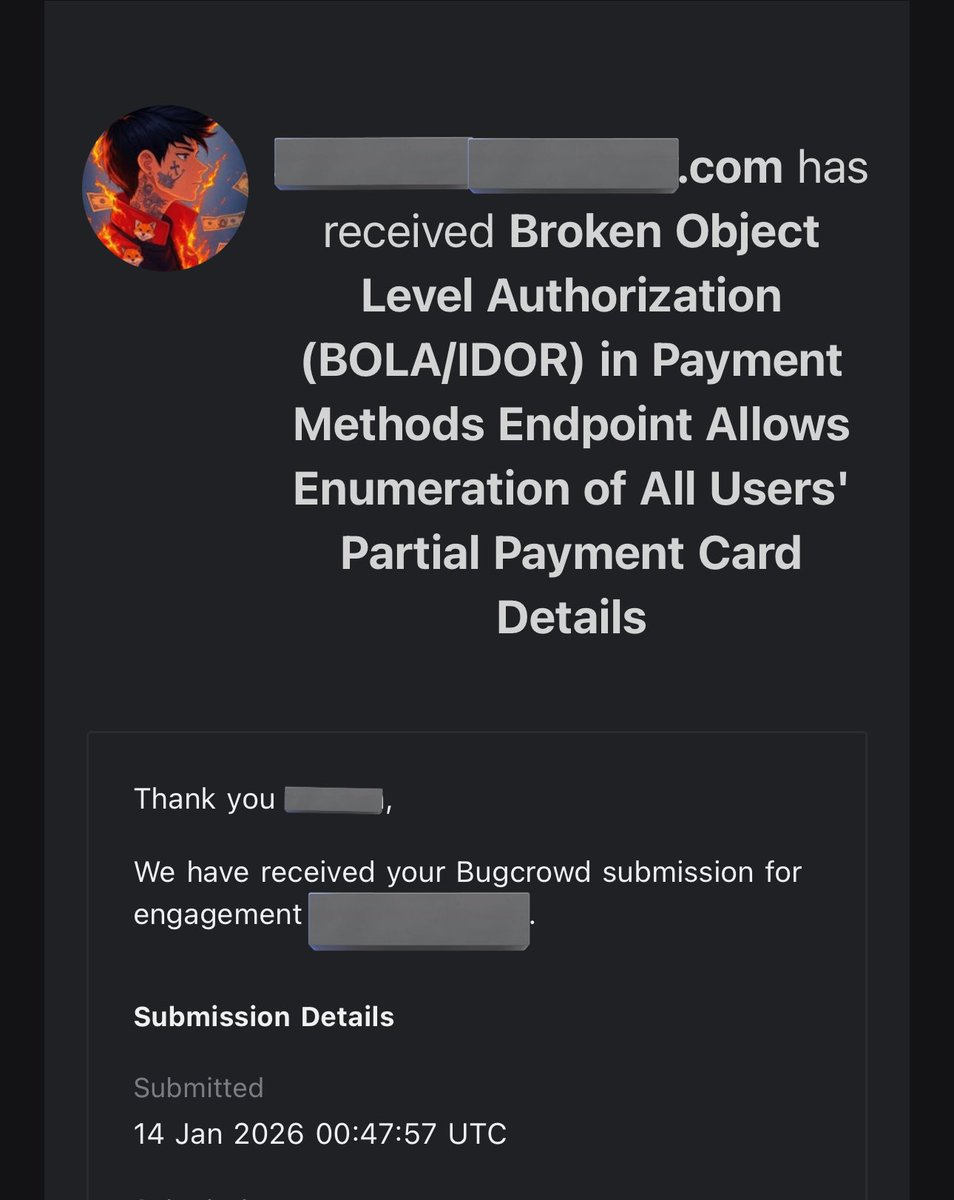
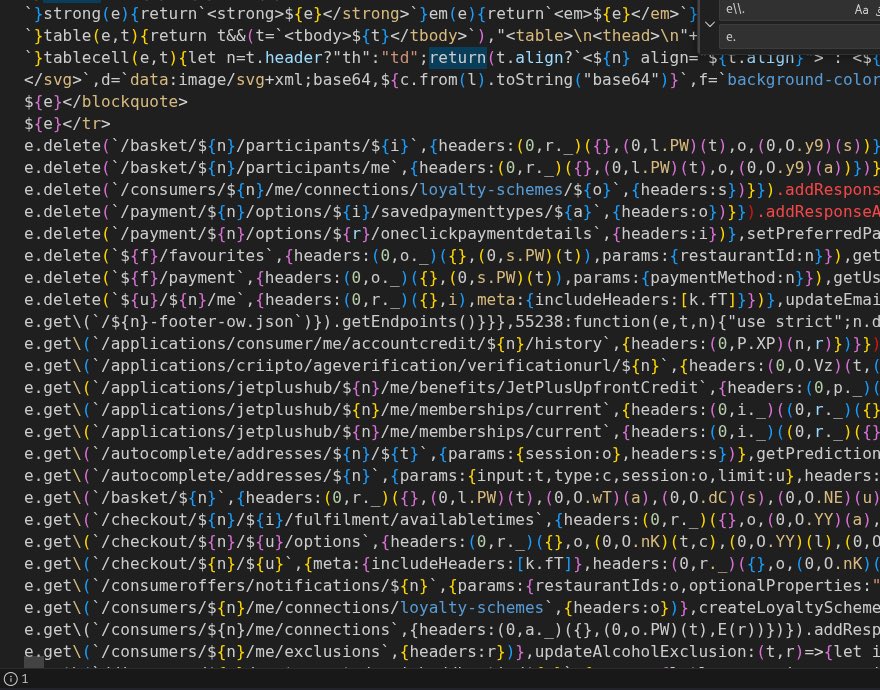
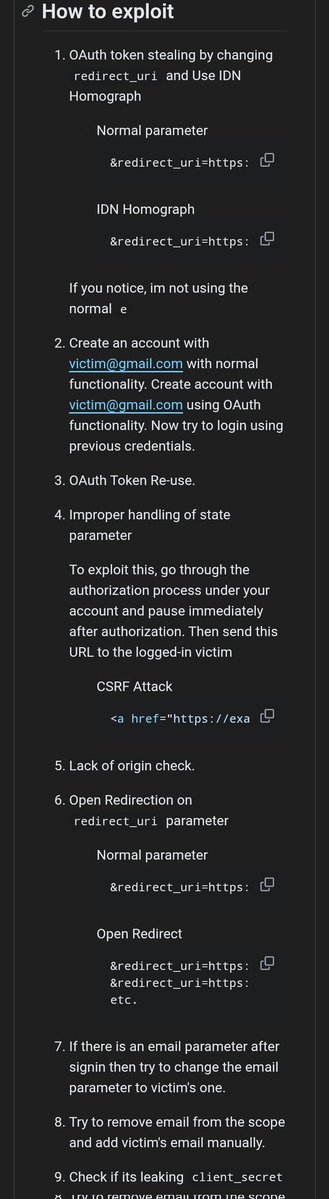
OAuth-based vulnerability is when the configuration of the OAuth service itself enables attackers to steal authorization codes or access tokens associated with other users’ accounts. By stealing a valid code or token, the attacker may be able to access the victim's account. https://t.co/Yvd57QwS3j
0
10
58
3.9K
48
7.5K
Total Members
+ 3
24h Growth
+ 37
7d Growth
Date Members Change
Feb 10, 2026 7.5K +3
Feb 9, 2026 7.5K +3
Feb 8, 2026 7.5K +3
Feb 7, 2026 7.5K +3
Feb 6, 2026 7.5K +21
Feb 5, 2026 7.4K +4
Feb 4, 2026 7.4K +8
Feb 3, 2026 7.4K +2
Feb 2, 2026 7.4K +2
Feb 1, 2026 7.4K +2
Jan 31, 2026 7.4K +6
Jan 30, 2026 7.4K +2
Jan 29, 2026 7.4K +0
Jan 28, 2026 7.4K —
No reviews yet
Be the first to share your experience!
Share Your Experience
Sign in with X to leave a review and help others discover great communities
Login with XLoading...
Learn how to perform Bug Bounty and Earn Money
Community Rules
Be kind and respectful.
Keep posts on topic.
Explore and share.